Security
The purpose of a hardware wallet is to store private keys offline in a secure envoriment.
KeepKey provides top-notch security and protects against both physical & virtual theft. It can be used on any computer, even one that’s been infected with malware or targeted by hackers.
Think of it as a tiny computer that’s built specifically to store Bitcoin private keys.
In addition to offline storage, KeepKey’s pin code and number randomization makes sure that 1) your wallet is secure from physical theft and 2) that a hacker couldn’t steal bitcoins from your wallet with malware. Watch the video below for an example of the pin protection:
KeepKey is an HD wallet, meaning your entire wallet can be backed up with the 12 words generated on setup. 12 words is the default setting, although KeepKey supports seed lengths of 18 and 24.
The seed is generated using entropy from both the device itself and the computer used for setup. The seed is generated offline on the KeepKey and displayed on the device’s screen. The device’s offline screen makes sure the seed is never displayed on an internet-connected device.
You can recover your wallet using the backup seed if your device is lost, stolen, or damaged. Recovery can be done with KK’s Chrome extension. Make sure to keep multiple backups of your seed and follow other best practices.
The wallet’s screen helps confirm you’re sending to the intended recipient, but does not prevent phishing attacks.
Setup and Initialization
The KeepKey is actually very easy to setup. It only takes a few minutes. Here is an example:
Privacy
As with any hardware wallet, using your device is only as private as the software wallet it’s used with. Electrum, KeepKey Chrome, and MultiBit HD support KeepKey. Electrum is the most private of the three.
KeepKey Supported Coins
According to its website, KeepKey only supports Bitcoin, Litecoin, Dogecoin, Namecoin, Testnet, Ethereum, and Dash.
Does KeepKey Support Ripple?
KeepKey cannot store Ripple at this time. Many users are asking on reddit, so it will likely be one of the next coins the company adds.
Converting Coins within the Wallet
KeepKey was acquired by ShapeShift. Since then, they have added a new feature that allows you to trade tokens directly on your KeepKey. This means you can make trades without having to create an account on an exchange.
KeepKey vs. TREZOR
KeepKey is actually a port of the TREZOR’s code and firmware.
There is no huge difference besides that TREZOR has been around much longer. The design of the two devices also differ. KeepKey has a more premium feel, is aluminum, and heavier. TREZOR is plastic and lighter. TREZOR is very light and may be more drop-proof than KeepKey.
KeepKey vs. Paper Wallet
KeepKey may be better than a paper wallet for less technical users. Paper wallets can be hard to setup and it’s easy to make mistakes. With KK it’s easier to create secure offline storage. Paper wallets are just as secure if created correctly, though.
KeepKey Promo Code
There are currently no KeepKey promo codes available. If a coupon or discount code becomes available we’ll update this post.
Does KeepKey Work with Litecoin?
KeepKey can be used to store Litecoin, DASH, and other altcoins. It’s up to software wallet developers to integrate support–the device itself is compatible with any altcoin.
Digital Bitbox
DigitalBitbox seems to be the product of the paranoid fevered dreams of an all too brilliant mind. Most true aficionados of cryptocurrencies tend to err on the side of caution where security is concerned.
By comparison, the makers of DigitalBitbox live there permanently. By no means is that a bad thing as Shift Devices may have created the most secure cold storage device for cryptocurrencies outside of a paper storage.
Not only is the DigitalBitbox a very well-guarded device, but it also brings a host of other features that really help to extend its usage and set it apart from the competition.
The First Rule of DigitalBitbox is Security
Like most cold storage devices for crypto-assets, DigitalBitbox looks like a standard USB flash drive. The one thing that sets it apart from hardware wallets is the micro SD card embedded horizontally in the middle. Not only does this feature set it apart visually, but also functionally.
The chief selling point of this hardware wallet is that you no longer have to write down several passphrases to recover your assets in case of an emergency. Rather, when you first setup the DigitalBitbox all this information is automatically stored on the SD card. No doubt, this has the potential to save many investors headaches in the future. Granted, you must still ensure that the SD card is kept somewhere safe and you should only ever have into inserted in the DigitalBitbox on setup or when resetting.
The Second Rule of DigitalBitbox is . . . Also, Security
Beyond this great security feature, this new hardware wallet comes with a bevy of other features that either improve its overall security or extend its use beyond just storing your Bitcoins. Foremost amongst these features is the ability to create a secondary “hidden” wallet: marketed as “Plausible Deniability” by the manufacturer. The main idea here being that should store most of your assets in one less accessible wallet and the rest of them in the more visible one. If for some reason the more visible wallet is compromised, the hidden wallet and your main resources stay intact. With the aid of the micro SD card, you can regain access to them later.
Additionally, the DigitalBitbox has two modes of twin factor authentication. First, when paired with another device, you can enable two-factor authentications for using the wallet to make new transactions. Alternatively, you can use the DigitalBitbox itself as the second factor for another platform that uses two-factor authentications. It should be noted that doing this does disable some other options on the wallet. Ideally, only the first mode of twin authentication should be used if your DigitalBitbox is your main hardware wallet. However, if you don’t intend to use it for making many transactions, then it makes for a useful extended feature.
A New Competitor for the Trezor and Ledger
When it comes to using cryptocurrencies, if security dominates your every thought, then the DigitalBitbox is the hardware wallet that you are looking for. It is exceptionally easy to engage with and it utilizes open source applications for Linus, Mac, and Windows. The only real downside for prospective users is that for all intents it is currently restricted to Bitcoin. Otherwise, it novel new platform that offers solid functionality and comes at a very competitive price.
OpenDime Hardware Wallet
Recently, there has been a lot of excitement around Bitcoin and other altcoins. It is understandable that some newcomers have the impression that Bitcoin is some sort of collectible item, yet the fact remains that Bitcoin is simply a currency. Stripped of all the hype and value predictions, Bitcoin is primarily a means of exchange. OpenDime is a relatively new cold storage platform that truly embraces the values of decentralization and relative anonymity. In an era where highly, accessible centralized hot exchanges are all the rage, OpenDime hearkens back to a purer philosophy and with it brings its own new take on hardware wallets to the marketplace. OpenDime is made by the same company that makes Coldcard.
Cold Hard Bitcoin Sticks
OpenDime is the making a name for itself as the “piggy bank” of cold storage units in the world of cryptocurrencies. It functions like other cold storage units with one key exception: one-time secure usage. That one key difference changes quite a lot in the way people use it. Other storage platforms act more like wallets to be used repeatedly with a reasonable degree of security. Whereas an OpenDime unit can be used extremely securely as an address to store Bitcoins until the owner needs to cash out, but only once. In a manner that directly parallels smashing open a piggy bank, once an OpenDime storage unit is “opened” it can no longer be used with the same degree of safety again. OpenDime is a platform that changes the intangible asset of Bitcoin into a physical thing that people can exchange between each other in the real world.
The Setup
OpenDime works in a similar fashion to most cold storage units. You buy it, you initialize it, then you use it. The one add-on to this process is that when you want to cash the funds stored on it, you literally have to break it open.
The initialization process is relatively simple. Plug it into a USB port on your device. You will then have to generate a private key by adding 256 KB to the drive. You can do this by dragging one or two random pictures into it. After the private key is generated the drive will self-eject. It is now ready to use. To manage your assets and view your digital address you will have to open the index.htm file located on the drive. The user interface is very easy to use and even provides links to several blockchain browsers.
Making Your Bit-Omlet
Eventually, you will want to access the Bitcoins or Litecoins stored on it. If you have the first version of OpenDime, you will need to break off a plastic "tongue" in the middle of the flash stick. Later versions work much like resetting old routers. You will need to push a pin through a marked section of the drive. Both of these processes physically change the drive. After doing this the private key associated with that OpenDime will be downloaded onto your pc or mobile device. This is the most vulnerable point in using the OpenDime. Make sure that you are using a secured system when doing this. You can then use the private key to access your funds in the same way you would with any other platform.
Security Risks with Hardware Wallets
Hardware wallets are more secure than any other software wallet, like one that runs on your Android or iOS device, or desktop. However, hardware wallets have some unique security risks to be aware of.
Tampering of the Device
We always recommend to order directly from the hardware seller. This is because someone can buy a hardware wallet, tamper with it, and sell it used. They could program it to steal any bitcoins or add a back door.
Most hardware wallets add some special kind of tape on the packaging to try to make any tampering more noticeable. This is another reason we recommend only ordering from the hardware wallet company, and not from a website like eBay.
Bad Random Number Generator
Bitcoin private keys are based on cryptography. Random number generators, also called RNGs, are used to create the private keys that secure bitcoins.
If the random number generator is not random enough, that means someone else can recreate the private key of the hardware wallet easier. This attack has happened in the past with blockchain.info, a web wallet. Over 300 BTC were lost because blockchain.info did not use good RNG, so a hacker was able to generate the private keys again and steal coins.
One way to help prevent this is to use the hardware wallet’s custom 25th word. TREZOR, for example, allows you to add a 25th word to the 24 word seed. This means that you can technically add your own RNG to the computer generated RNG to ensure your private key will be truly based on good RNG.
What happens if the hardware wallet company goes out of business?
All hardware wallets listed above work with other wallets. So, if the hardware wallet company goes out of business you will still be able to use your wallet with a different wallet like Electrum.
Let’s say you use TREZOR with TREZOR’s myTREZOR wallet. TREZOR goes out of business and no longer supports myTREZOR wallet and it gets shut down.
You could, in just a few minutes, download Electrum on your computer. Once installed, you’d setup your TREZOR and all of your transaction history and balance would get imported and be exactly the same. This is because Electrum will use the same 24-word seed you generated with TREZOR on setup.
Which wallets can be used for each device?
Ledger Nano S, KeepKey and TREZOR all work with:
- Mycelium (Android version only)
- Electrum for Mac, Windows and Linux
- GreenAddress
Do these hardware wallets work for Ethereum?
Yes, all of these wallets work with Ethereum, Litecoin and many other coins.
TREZOR and Ledger both have blog posts explaining their integrations with various Ethereum wallets.
The hardware wallet tells me to write down the 24 word seed on paper.
Should I take a picture of the seed with my phone as a backup?
NO, NO, and NO!
The seeds generated by hardware wallets are meant to be written down only. By taking a picture of your seed with an internet connected phone, you put your entire wallet on a device that is connected to the internet and easier for hackers to get into. Please do not do this!
Why do the hardware wallets have buttons?
The buttons are used to confirm transactions. In order to send a transaction, you must physically press or hold buttons on the devices. This is a security feature. If a hacker were to access the hardware wallet somehow, the hacker still would not be able to send a TX without physical access to the buttons. Read more about this in TREZOR’s security philosophy.
Do hardware wallets work with Coinbase?
One of the most frequent questions we get asked is how Coinbase works with hardware wallets.
It’s a trick question!
Coinbase does not work directly with hardware wallet. You should, however, send bitcoins from Coinbase directly to your hardware wallet once you buy. Never store bitcoins on Coinbase or any other exchange for long periods of time.
Too many people in the past have lost money from hacks like Bitfinex and Mt. Gox.
So, yes, use a hardware wallet in conjunction with Coinbase. Buy on Coinbase, then send to hardware wallet.
Also, what we said above goes for ALL exchanges. Use Bitstamp? Cool! Once you buy bitcoins on Stamp, send the coins to your hardware wallet. The same goes for Kraken, Poloniex, or any other exchange or service that holds your coins!
Note on Hardware Wallets
Note that to use a Bitcoin/cryptocurrency hardware wallet you need a software wallet to interact with the device.
All of the hardware wallets have default software wallets made by the company. However, you can also install separate software wallet to use the hardware wallet with an altcoin.
A basic example is that TREZOR’s own wallet supports Bitcoin, but you can also use Electrum to use your TREZOR with Bitcoin.
One may want to do this because Electrum has some unique features that TREZOR’s wallet doesn’t have, like spending from specific outputs or “freezing” certain addresses so they can’t be spent from.
Another important reason for installing other software wallets is to hold other non-supported tokens. For example, the default Nano Ledger S software wallet can hold Ethereum, but it cannot hold other ERC20 tokens.
In order to hold ERC20 tokens on the Ledger Nano S, you have to install a 3rd-party software wallet, such as MyEtherWallet (MEW). After installing MEW, you will be able to store ERC20 tokens on your Ledger Nano S.
Several hundred ERC20 tokens exist, so downloading a software wallet can massively increase your hardware wallet's functionality.
Best Altcoin Hardware Wallets
If you are serious about using and investing in various cryptocurrencies, then you will need to get a hold of a hardware wallet, possibly more than one. All financial instruments are inherently risky. Cryptocurrencies tend to be riskier than most in a variety of ways. While it is impossible to eliminate all risk when using them, hardware wallets go a long way to reducing most. However, not all hardware wallets are created equal. It is not enough to buy just anything, but rather you need to carefully select the right option for you. For years there was little choice for cold storage options, but now there is more than ever. In this article we will take a look at the best on the market at the moment and why you should invest in them.
The Cool Wallet
The Cool Wallet is a recent addition to the cold storage marketplace and offers its own interesting take on things. Its looks certainly hold up to the first part of the brand name, but considering its form factor, it's more of a crypto-credit card than a wallet.
The Cool Wallet also handles quite well when compared to other cold storage devices. Further, it has a very unique approach to passphrases compared with the norms for other hardware wallets. This device generates random 20 random numbers, as opposed to words, and even gives you the option to have them sent to one of your devices. Still, it is highly advisable to simply write them down instead.
Cool Wallets are also inherently two factor authenticated, as they must be paired with another blue tooth enabled device to function. For some, this may be a possible security concern, but not hugely so, especially given the highly randomized “pass-numbers” and authentication process.
In terms of design, this is maybe the best option and also great as a backup hardware wallet to handle small amounts of cryptocurrencies.
Supports: Bitcoin, Bitcoin Cash, Ethereum, Litecoin, Ripple
DigitalBitbox
DigitalBitbox is one of the most secure packages that you could purchase. It sacrifices quite a bit in terms of its physical interfacing, but more than makes up for that with its multi-platform open source software and an immense range of features.
One of the best things about the DigitalBitbox is its unique adaptation for passphrase security and backups. This is maybe the one device out there, that comes with a simple yet truly reliable “second-chance” in the worst-case scenario. Additionally, it comes with multiple layers of added security including a hidden wallet and two-factor authentications.
It also helps that it is one of the most affordable options out there at the moment. The only real drawback for the DigitalBitbox is its lack of support for most altcoins. That being said, if you are only or primarily using Bitcoin, then this is the hardware wallet for you.
Supports: Bitcoin
Ledger Nano S
Currently, the industry leader in hardware wallets is the Ledger Nano S platform and it’s not hard to see why. This hardware wallet supports a large number of different cryptocurrencies and has a robust array of security features.
Ledger’s main competitor in the market space is the original Trezor hardware wallet. One of the key advantages of the Ledger over the Trezor is the freedom to create your own unique passphrases. Both the Ledger and the Trezor require 20 passphrases for recovery and reset purposes; however, the Trezor package sends the user a random list. The Ledger gives the user the freedom to create their own. Additionally, if aesthetics matter to you, the Ledger sports an arguably sleeker design than the Trezor.
The Ledger Nano S is definitely a safe place to start with hardware wallets, especially if you are just switching from using a hot wallet. In many ways, it represents the “CoinBase.com” of hardware wallets. If you are uncertain of where to start, this is probably for you.
Supports: Bitcoin, Bitcoin Cash, Bitcoin Gold, Ethereum, Ethereum Classic, Litecoin, DASH, Dodgecoin, Ripple, Komodo, PoSW, ARK, Expanse, Ubiq, PIVX, Vertcoin, Viacoin, Neo, Stealthcoin, Stratis, Zcash
Trezor
Launched back when Bitcoin was just coming out of its infancy, the Trezor was the first ever commercially available Bitcoin hardware wallet. Although many competitors have stepped forward over the years, it still remains one of the best hardware wallets for cold storage of cryptocurrencies.
As mentioned earlier, the Ledger is the main competitor with the Trezor for dominance in the marketplace. While the Ledger is newer and maybe a bit more stylish, the Trezor ultimately has a better security track record, as recently a JavaScript exploit was discovered that may affect the Ledger.
In a sense the Trezor is less “high-tech” than many other platforms; however, this makes it far less vulnerable. Additionally, a very nice feature of the Trezor is its semi twin factor randomized pin code generator that is required to be used before each use. On its own, it is quite resistant to any form of malware, but with this feature, you are protected from keyloggers as well.
Supports:
Bitcoin, Bitcoin Cash, Ethereum, Ethereum Classic, Litecoin, DASH, Dodgecoin, Namecoin, Zcash, ERC-20 Tokens
A Few Words
Depending on your aims, lifestyle, and preferences you may prefer one or more of the hardware wallets listed. Regardless of which you choose, it is simply important that you choose at least one and use it. The security of your Bitcoins and other altcoins is in your hands.
We can both agree that finding the right cryptocurrency wallet can be confusing.
But, don't worry: we've gone through all of the wallets and listed the best choices.
Today we're going to make it easy to decide which wallet is best for you. Read on!
Cryptocurrency Hardware Wallets
Hardware wallets are small devices that are plugged into your computer or phone. The hardware wallet generates your private keys securely in an offline environment. The innovation is that many wallets generate private keys on internet connected devices like computers or mobile phones.
By generating your private keys on an offline device, your keys are out of the reach of hackers.
Advantages:
- Private keys aren't exposed to your computer
- Hardware wallets cannot receive computer viruses or malware
- You must have the hardware to confirm a transaction, preventing remote hacking
- Most hardware wallets are encrypted with a PIN or other security feature
- If you lose your hardware wallet, you can still recover your coins
Disadvantages:
- Not free
Overall, hardware wallets are the safest type of wallet, with many security features built-in as well as support for many different types of cryptocurrencies. If you have significant crypto holdings that you want to store securely, you should strongly consider getting a hardware wallet.
Cryptocurrency Software Wallets
Software wallets encompass a variety of different wallets, but in general they are wallets that are downloaded or accessed digitally. These wallets include online/web wallets, desktop wallets, and mobile wallets.
Each type of software wallet has varying levels of security and accessibility, however, generally hardware wallets tend to be the safer but pricier option.
Due to the variety in software wallets, we will cover each type individually in more detail below.
Hot and Cold Storage

Before continuing, it is important to note the difference between hot and cold storage.
Hot storage refers to any type of wallet that is connected to the internet, while cold storage is any type of wallet that does not have internet connection.
Hot storage is very convenient and accessible, however, it is much less secure than cold storage. Any time a wallet is connected to the internet, it has the potential to be hacked. Cold storage remedies this problem at the expense of convenience.
Some software wallets can be hot or cold storage. If you download a desktop wallet on an internet-connected computer, it is hot storage. If you download the same wallet onto a device then disconnect from the internet, it becomes cold storage. Hardware wallets are always cold storage, with the convenience of a hot wallet.
Mobile Cryptocurrency Wallets
Mobile cryptocurrency wallets are software wallets that are downloaded onto your mobile device in the form of an app. The app stores your cryptocurrency. These wallets are simple and easy to use, and work well for people who pay for transactions using cryptocurrency.
Mobile wallets are safer than online wallets, but are still vulnerable to hacks.
Advantages:
- Straightforward and easy to use
- Great for people who buy items often with cryptocurrencies
- Some wallets have additional features such as QR code scanning or the use of near-field communication technology
Disadvantages:
- Your wallet could be hacked, especially if your phone is consistently connected to the internet
- If someone steals your phone, they could access your wallet
Coinomi Mobile Wallet
Coinomi is another multi-cryptocurrency wallet that is available for iOS and Android.
Coinomi supports currencies such as:
- Bitcoin
- Dash
- Dogecoin
- Ethereum
- Ethereum Classic
- Litecoin
- Zcash
Coinomi is also integrated with ShapeShift and Changelly, another cryptocurrency exchange website.
Coinomi also offers One-Time Backup. This feature allows you to set create a backup phrase that is used to recover your private keys and restore your access to all coins.
Jaxx Mobile Wallet
Jaxx is a popular option for a multi-cryptocurrency wallet for iOS and iPhone.
Jaxx supports a number of cryptocurrencies, including:
- Bitcoin
- Litecoin
- Ethereum
- Ethereum Classic
- Dash
- Zcash
The wallet is integrated with ShapeShift, so you can actually exchange coins from within the wallet.
Jaxx is also available for Android.
Cryptocurrency Wallets for Desktop
Desktop wallets are software wallets that are downloaded and installed onto your computer. These wallets store your private keys on your hard drive. This makes them safer than web wallets. However, if your computer is connected to the internet, your wallet is still vulnerable to attacks.
Advantages:
- You hold your own private keys, as opposed to a 3rd-party, which reduces your chances of being hacked
- Desktop wallets are easy to use and offer a variety of features
- You can create a cold storage wallet by disconnecting your computer from the internet
Disadvantages:
- If your computer has internet access, your wallet is at higher risk
- Your keys are held offline, so if your computer breaks, you could lose your funds
- Regular back-ups are required to prevent the above from occurring
- If your computer is infected with viruses or malware, your wallet could be hacked
Using a desktop wallet allows for greater security than a web wallet, and a number of different features. If you plan to store large amounts of currency on a desktop wallet, you should certainly place it in cold storage.
Exodus Wallet - Desktop Wallet

Exodus is another popular multi-cryptocurrency wallet or universal cryptocurrency wallet, meaning it supports many coins. Like other desktop wallets, your private keys are stored on your computer.
Exodus is also integrated with ShapeShift, so you can swap your coins within your wallet.
Exodus supports the following cryptocurrencies:
- Bitcoin
- Litecoin
- Ethereum
- Dash
- Golem
- OmiseGO
- Decred
- More Here
Exodus is not entirely open source, however, so it is not as trustworthy as a fully open source wallet.
Atomic Wallet

Atomic Wallet is a new multiple currency wallet that allows you to manage Bitcoin, Ethereum, XRP and over 300 coins and tokens easily.
Some of the wallet's best features are:
- Encrypted private keys that never leave user device
- Option to buy crypto with a bank card in 20-30 minutes
- Built-in Atomic Swap decentralized exchange
- Instant exchange via Changelly and Shapeshift
Jaxx Desktop Wallet
Jaxx, the iOS and Android wallet we mentioned above, is also available for desktop. Jaxx is not open source, but the code is viewable on their website.
The desktop version supports the same currencies previously listed, and also has ShapeShift integrated. Jaxx stores your private keys on your computer.
Online Cryptocurrency Wallets

Online wallets, or web wallets, are wallets that are accessed through your web browser. These wallets store your private keys in the cloud. Exchange wallets such as Coinbase are a type of web wallet.
Web wallets allow you to quickly access your coins from any internet connected device. However, because a company holds your private keys, you have no control over your wallet. These companies could take use your private keys to steal your currency, or their servers could be hacked.
Advantages:
- Instant access to your wallet
- Any device with internet can be used to access your coins
Disadvantages:
- You don't control your private keys
- Companies can be hacked or steal your coins
We highly advise against web wallets, as they are by far the least secure type of wallet. Do not store a large amount of currency in web wallets, and do not use them for long term storage.
MyEtherWallet - Online Ether and ERC20 Wallet
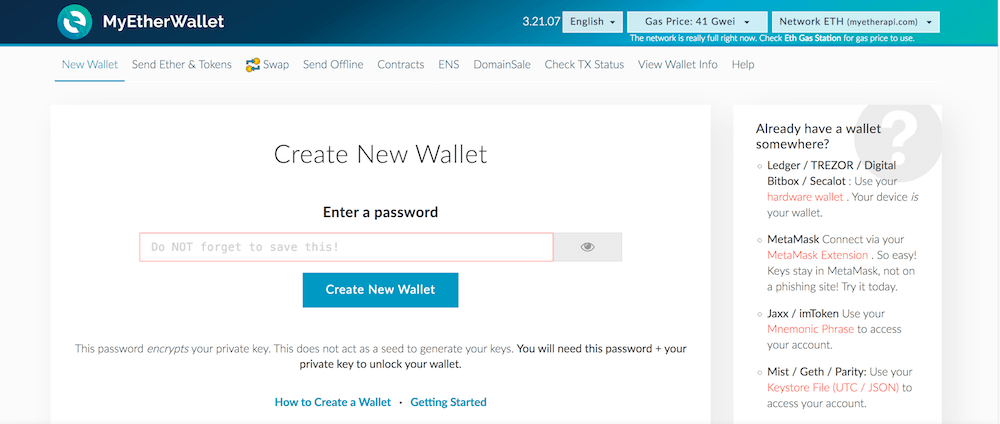
Advantages:
- Integration with hardware wallets like Ledger Nano S has made the combo of Ledger Nano S + MEW the most popular way to store Ether and ERC20 tokens
- Clean interface makes it easy for new users to use, with or without a hardware wallet
Disadvantages:
- Without a hardware wallet, it is a web wallet so should not be used with large amounts
MyEtherWallet (MEW) is an open source wallet that was launched in 2015. This software wallet is one of the most popular options for users looking to store Ethereum and other ERC20 tokens.
Notably, MyEtherWallet cannot store Bitcoin, Bitcoin Cash, or other related currencies. It is solely for Ethereum based coins.
MyEtherWallet generates private keys locally, so they are not stored on MEW servers. This increases security and puts control of the wallet into your hands.
Wallet Reviews and Guides
The next section will go over some popular cryptocurrency wallets.
MyEtherWallet (MEW) Guide
Creating a MEW wallet is a relatively simple process. The first step is to visit the MyEtherWallet homepage. Be sure the website domain is exactly correct to avoid spoofing websites. You should also bookmark the website to prevent this problem in the future.
On the home page, enter a password, then select the "Create New Wallet" button. MyEtherWallet will then generate a "KeyStore" file in UTC/JSON format. This is your password protected private key.
Select the "Download KeyStore File (UTC/JSON)" button, then click "I understand. Continue."
The KeyStore file will be downloaded, and you will be able to view your private key on the next screen. You should save the KeyStore file to an offline hard drive, or a flash drive that you do not use online.
After clicking "Save your Address", you will be prompted to unlock your wallet to see your public wallet address. In the selection screen, choose "KeyStore / JSON File".
Select the KeyStore file that you previously saved, then enter the password you used to create your wallet initially.
The benefit of using a KeyStore file is that you don't have input your entire private key, just the password that encrypts the file. However, this process is not entirely safe, as you are giving your private key file to a website.
A safer alternative is running MyEtherWallet offline.
This is a bit more complicated, but may be worth it for the extra security. First, download. Click on "etherwallet-vX.X.X.X.zip" to download, then move the file to a flash drive.
Plug the USB stick into a computer with no internet access and extract all the files from the drive to the computer. Within the MyEtherWallet folder, select index.html to open the wallet.
This will open MyEtherWallet in your browser. You will be warned that you can't connect to the network, but that is normal. When using the wallet in this manner, you won't be able to view your Ether or other token balances, but they can still be viewed with Etherscan.
Note: MyEtherWallet was recently the target of an elaborate hack.
Exodus Wallet Setup Guide
In order to set up an Exodus wallet, first visit the Exodus website. Select the "Download" button, then choose your operating system.
Run the file that downloads and install the wallet. In order to fully set up your Exodus wallet, you have to deposit some cryptocurrency.
Select the "Wallet" tab on the left side of the screen. Select the cryptocurrency you wish to deposit, then click "Receive". Your deposit address will be displayed and you can select the copy button.
Open the exchange or wallet you are sending the cryptocurrency from and paste the deposit address. After sending the cryptocurrency, you should be able to see it arrive in the Exodus wallet.
Once it arrives, select the "Backup" tab. Create a password and continue. Exodus will then reveal your 12 word recovery phrase that you can use to recover your cryptocurrencies. Write this phrase down and store it away safely.
Next, create a backup link by entering your email address. You can follow this email link then enter your password to regain access to your Exodus wallet.
With these fail-safes in place, your wallet is all set up.
Jaxx Desktop Wallet Guide

Jaxx, the iOS and Android wallet we mentioned above, is also available for desktop. Jaxx is not open source, but the code is viewable on their website.
The desktop version supports the same currencies previously listed, and also has ShapeShift integrated. Jaxx stores your private keys on your computer.
To set up a Jaxx wallet for desktop, first go to their website, then select the downloads tab. Select the desktop version.
Once the wallet is downloaded and installed, the first screen you will see is the release notes. Select "continue" then agree to the terms of service. In the next screen, select "Create New Wallet", then continue. Then, select the custom option, as this allows you to set up security features and other preferences.
You can then select which cryptocurrency wallet(s) you would like to create. You must select at least one, but you can add or remove more at any time later on. You will then be asked to select the a fiat currency. The value of your coins will be listed in this currency.
Jaxx will then ask if you'd like to create a wallet back up now. Select yes, and it will generate a 12 word backup phrase. Like the other backups, be sure to write it down and store it in a safe place.
You'll then be required to type your backup phrase into the Jaxx wallet to ensure you did not just skip through that step.
Finally, you can set up a 4-digit security which will allow you to access your wallet regularly.
Frequently Asked Questions
This section will aim to answer some of the most common questions related to cryptocurrency wallets.
Which wallet is best for me?
The cryptocurrency wallet that is best for you will depend on what you’re using cryptocurrency for.
If you just need a wallet for some small, infrequent payments then using one of the Android, iPhone or desktop wallets mentioned above would be fine.
If you are investing in cryptocurrency and need secure storage for your funds, then a hardware wallet like Ledger or TREZOR will better fit your needs.
What about paper wallets?
Paper wallets are a cheap way to create secure storage for crypto. The main issue is it’s very confusing and hard to do right. This is why we don’t cover it in this post. If you want to use a paper wallet, please do your own digging on Google.
How do I add funds to my wallet?
You’ll have to first buy cryptocurrency on an exchange and then transfer the coins from the exchange to your wallet. This is the only way to fund your wallet.
Some wallets allow you to buy bitcoins from within the wallet, but there is yet to be a wallet that allows you to buy a coin other than Bitcoin.
Is Coinbase a good wallet?
Coinbase is an exchange and should not be used as a wallet. Coinbase is definitely a trusted place to buy bitcoins, but once you do so move your Bitcoin, Litecoin or Ether off the site into one of the wallets discussed in this post.
Is Robinhood a good wallet?
Robinhood is not a Bitcoin wallet. You are not able to withdrawal your coins from their app.
How do I get a cryptocurrency address?
Your wallet will automatically generate addresses for you. Each crypto has slightly different formats for the addresses.
Bitcoin addresses start with a 1 or 3 and look something like this:
- 1BvBMSEYstWetqTFn5Au4m4GFg7xJaNVN2
- 3J98t1WpEZ73CNmQviecrnyiWrnqRhWNLy
Ethereum addresses start with a 0 and usually look something like this:
- 0xde0B295669a9FD93d5F28D9Ec85E40f4cb697BAe
Litecoin addresses start with an L and usually look something like this:
- LVXXmgcVYBZAuiJM3V99uG48o3yG89h2Ph
How do I open a cryptocurrency account?
There is no such thing as a cryptocurrency account.
You can have a wallet, which stores your coins.
You can create an account on a cryptocurrency exchange, but this is not a default cryptocurrency account in the same way that you have a bank account.
Any common mistakes to be careful of?
The biggest mistake we see people make is to store money on exchanges. Then the exchange gets hacked or exit scams and people lose their money.
DO NOT STORE YOUR MONEY ON AN EXCHANGE!
Cryptocurrency Security Advice
This section will give you some tips on how to secure your cryptocurrency in many ways, whether your on an exchange or wallet.
The migration of value into the digital realm brings with it new challenges in terms of best security practices. As with any unit of value, there is always someone, somewhere that seeks to extract this value for their own ends, whether it be through coercion, social manipulation or brute force.
This guide is intended to provide a broad overview of the best practices for securing your crypto assets. While most of these steps are not mandatory, following them will greatly increase your financial security and peace of mind in the crypto world.
Passwords — Complexity & Re-Use
Starting from the ground up, password complexity and re-use are two major pain points that many average users do not consider adequately. As you can see by this list, average password complexity still leaves a lot to be desired. The less complex your password is, the more susceptible to hack your account is. If you use the same passwords, or even slight variations of the same passwords across multiple accounts, your chances of compromise are greatly increased.
So what can you do? Fortunately the fix for this is relatively easy. Use randomly generated 14 character+ passwords and never re-use the same password. If this seems daunting to you, consider leveraging a password manager such as LastPass or Dashlane that will assist in password generation and storage.
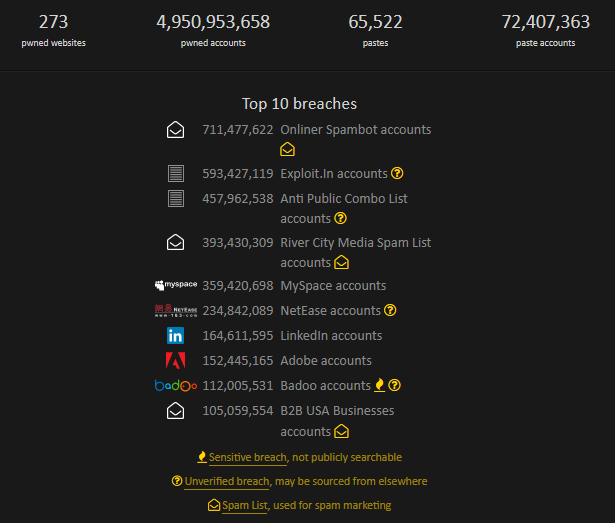
You can find out if any accounts associated with you have ever been compromised here as well as using this tool to test just how strong variations of your passwords may be (*do not use your real password on here, only similarly structured variations).
Dedicated Email Accounts
Almost every online service/exchange requires some type of email account association during the activation process. If you are like most people, you will probably use your default email that you’ve had for years, and perhaps add a bit more complex password for the account itself for good measure.
In most cases however, all a hacker needs is access to your emails in order to reset account passwords that may be tied to it. It’s as simple as navigating to the website/exchange and clicking the ‘forgot password’ link to begin the process. So, if you are like most people and have an email address that has been active for years, with a weak login password, your chances of being hacked are much higher.
For the above reasons, do yourself a favor and create a new/dedicated email address for use with your crypto accounts. Services like ProtonMail and Tutanota are free and offer end to end encryption without sacrificing usability (mobile app availability etc.). If you decide to stick with Gmail, consider activating the Advanced Protection Program that Google offers.
Two-Factor Authentication
We typically recommend setting up two-factor authentication (2FA) for any and every account that offers it, even if the service is not crypto related. All 2FA does is require a second means of confirmation that you are who you say you are when logging into accounts. Most typically this is in the form of something you know (password) and something you own (SMS code sent to phone).
While SMS is still the most common form of 2FA offered by online services, it is unfortunately the least secure. The following general use 2FA methods are ranked from most secure to least:
- FIDO U2F — This is a physical device that plugs into a USB port and requires a physical button touch to generate a unique 2FA access code. It is preferable because a hacker would need to have the device in their physical possession in order to access your account. Most hacks occur remotely which makes this our top 2FA choice (albeit not a panacea ).
- Google Authenticator — An app that resides on your mobile device and cycles through one-time use access tokens. If you go this route, be sure to save your backup code that is provided at initial setup. If you don’t have this and your phone is lost or broken then you have no way to get these code settings back.
- Authy — Similar to Google Authenticator but potentially less secure as you can re-access the codes from an alternate mobile device if your main one is lost or broken (this feature can be disabled but is active by default). While this may seem more ideal, what is more convenient for you is also more convenient for those who may be trying to hack you.
- SMS — Codes send to your cell phone through text message. Better than no 2FA at all, but susceptible to social engineering SIM attacks. Interestingly, SMS 2FA security holes did not come to light until the popularity of Bitcoin began to grow.
Secure Crypto Storage
If you don’t hold the private keys, you don’t own your money!
This category is how most people have been compromised and lost money in crypto. How? Primarily, by treating an exchange (Coinbase, Binance, Bittrex, Poloniex etc.) as a wallet to store their crypto assets in.
Mt. Gox, Bitfinex, BitGrail and Coincheck are just four out of a handful of crypto exchanges that have been hacked in the past 5 years, with the cumulative amount stolen exceeding $1 billion USD. While some users of these exchanges have been ameliorated to an extent, many are still suffering from the partial or even total loss of crypto funds that they held on these exchanges at the time of the hacks.
Our advice is to hold crypto on hardware or paper wallets that you alone control. If you wish to trade on exchanges, only do so with funds that you are potentially willing to forfeit entirely should either the exchange or your individual account become compromised.
A few of our recommended hardware wallet manufacturers are Ledger, Trezor, and Keepkey. You can find our more detailed wallet reviews here . As with all hardware/software, please ensure that your device firmware is kept up to date, as patches are pushed out continuously to address security concerns.
Mobile Crypto Wallets
Mobile app wallets such as Mycelium, BRD, Samourai, Cryptonator, etc. should be treated similarly to how you may treat your physical wallet/purse.
You only carry small amounts of discretionary spending funds in these wallets as they are more susceptible to loss or theft. Again, what is more convenient for you is more convenient for a malicious actor as well. Your phone is also susceptible to malware and should not be considered sufficiently safe for storing large amounts of funds.
Phishing Attacks
If you have crypto then you are an ideal target for phishing scams. Facebook and Twitter are just two of many avenues that hackers scour for potential victims. It has become common to see fake crypto exchange emails or ICO fundraising confirmations circulating such as the example below.
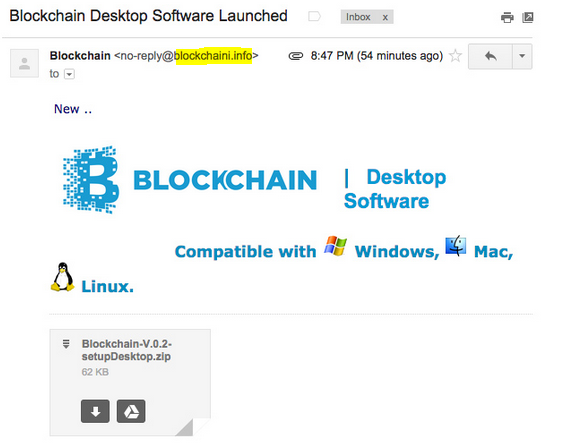
Phishing email impersonating Blockchain.info. Note send address & logo irregularity.
It is best to NEVER open suspicious attachments or provide credentials through email and to always closely inspect the logo, wording and send address of any emails received that pertain to financial accounts or that request sensitive information.
When in doubt, navigate to the legitimate exchange or web service that the email supposedly originated from and contact their support team to inquire on the validity of what you received before taking further action.
Clean Hardware
This brings us to the general best practices portion of this guide. Malware is everywhere on the internet and regardless of your attention to detail, sooner or later you are likely to fall victim to some type of malicious software. As such, it is best to have active antivirus subscriptions on your devices and to run periodic scans. I personally like to run Malwarebytes and Roguekiller on my PC once each week and have background scans on my phone that run each automatically. Generally speaking Windows is the least secure OS, primarily due to the fact that it is the oldest and most pervasive OS in use today. Many security conscious techies tend to prefer Linux or iOS for this reason.
Summary
Security on the web is akin to game of whack-a-mole and your level of security will likely scale accordingly with the amount of sensitive data (or crypto assets) that you are protecting.
While there is no such thing as an ‘unhackable’ system, there are valuable steps that you can take to drastically reduce your likelihood of compromise.
Always remember to:
- Use complex and unique passwords
- Create a separate/dedicated email account for crypto services
- Use two-factor authentication
- Store most (if not all) of your funds on hardware wallets
- Be wary of phishing emails
Good luck and stay safe!



0 Comments